Dealing with the Ransomware Scourge
Introduction
Ransomware is advanced malicious software (malware) that encrypts and holds your digital assets such as files or computer systems hostage, and demands ransom to regain access. Ransomware attacks can take only seconds to damage your valuable systems and data, potentially causing irreversible data loss and financial damage. Ransomware can be highly profitable for cybercriminals, and an increasing number are utilizing ransomware to extract money from victims. It is the fastest growing malware threat, targeting users of all types —from the home user to the corporate network.
Ransomware targets home users, businesses, and government networks and can lead to temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organisation’s reputation. Ransomware may direct a user to click on a link to pay a ransom; however, the link may be malicious and could lead to additional malware infections.
Protecting Your Networks
Educate Your Personnel
Attackers often enter the organisation by tricking a user to disclose a password or click on a virus-laden email attachment. Remind employees to never click unsolicited links or open unsolicited attachments in emails.
To improve workforce awareness, the internal security team may test the training of an organisation’s workforce with simulated phishing emails.
Proactive Prevention Is The Best Defence
Prevention is the most effective defense against ransomware and it is critical to take precautions for protection. Infections can be devastating to an individual or organisation, and recovery may be a difficult process requiring the services of a reputable data recovery specialist.
BDO recommends that users and administrators take the following preventive measures to protect their computer networks from falling victim to a ransomware infection:
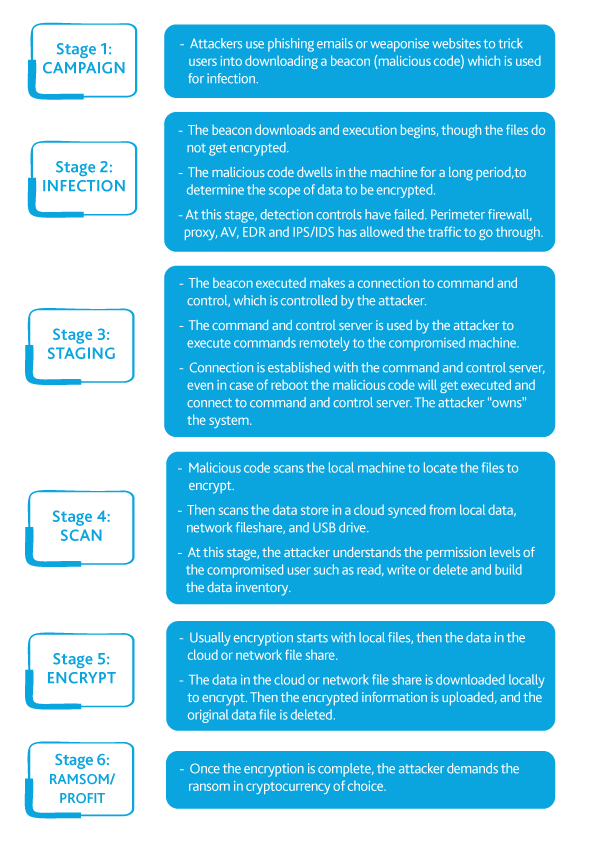
THE RAMSOMEWARE ATTACK STAGES
Methods Of Infection
Understanding how ransomware infects and spreads is the key to avoiding falling victim to an attack. Post-infection, ransomware can spread to other machines or encrypt network files in the organisation’s network. In some cases, it can spread across organisational boundaries to infect supply chains, customers and other organisations. All of the following can be vectors of infection for ransomware attacks:
- Phishing
- Compromised Websites
- Malvertising
- Exploit Kits
- Downloads
- Messaging Applications
- Brute Force via RDP
Preventive Measures
- Implement a security awareness and training program. Essentially, end users are targets, employees and individuals should be aware of the threat of ransomware and how it is delivered. Secure the human firewall.
- Enable strong spam filters to prevent phishing emails from reaching the end users and authenticate inbound email using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent email spoofing.
- Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
- Configure firewalls to block access/ blacklist to known malicious IP addresses.
- Update and patch operating systems, software, and firmware on devices. Consider using a centralised patch management system.
- Configure anti-virus and anti-malware programs to conduct regular scans automatically.
- Manage the use of privileged accounts based on the principle of least privilege: no users should be assigned administrative access unless absolutely necessary; and those with a need for administrator accounts should only use them when needed.
- Configure access controls—including file, directory, and network share permissions— with least privilege in mind. If a user only needs to read specific files, the user should not have write access to those files, directories, or shares.
- Disable macro scripts from office files transmitted via email. Consider using Office Viewer software to open Microsoft Office files transmitted via email instead of full office suite applications.
- Implement Software Restriction Policies (SRP) or other controls to prevent programs from executing from common ransomware locations, such as temporary folders supporting popular Internet browsers or compression/ decompression programs, including the AppData/ LocalAppData folder.
- Consider disabling Remote Desktop protocol (RDP) if it is not being used. All remote connections should be monitored or audit trailed.
- Use application whitelisting, which only allows systems to execute programs known and permitted by security policy.
- Execute operating system environments or specific programs in a virtualised environment.
- Categorise data based on organisational value and implement physical and logical separation of networks and data for different organisational units.
Business Continuity Considerations
- Back up data regularly. Verify the integrity of those backups and test the restoration process to ensure it is working.
- Conduct an annual vulnerability assessment and penetration test.
- Secure your backups. Ensure backups are not connected permanently to the computers and networks they are backing up. Examples are securing backups in the cloud or physically storing backups offline. Some instances of ransomware have the capability to lock cloud-based backups when systems continuously back up in real time, also known as persistent synchronisation. Backups are critical in ransomware recovery and response; if you are infected, a backup may be the best way to recover your critical data.
How Do I Respond To Ransomware?
Implement your security incident response and business continuity plan. It may take time for your organisation’s IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your organisation’s essential functions according to your business continuity plan. Organisations should maintain and regularly test backup plans, disaster recovery plans, and business continuity procedures.
Conclusion
Ransomware continues to mutate and evolve, with Ransomware-as-a-Service (RaaS) model now growing in popularity. Malware authors sell custom-built ransomware to cybercriminals in exchange for a percentage of the profit. The buyer of the service decides on the targets and the delivery methods. This malicious cycle and ergonomics are leading to increasingly targeted malware, innovation in delivery methods and ultimately a higher frequency of ransomware attacks.