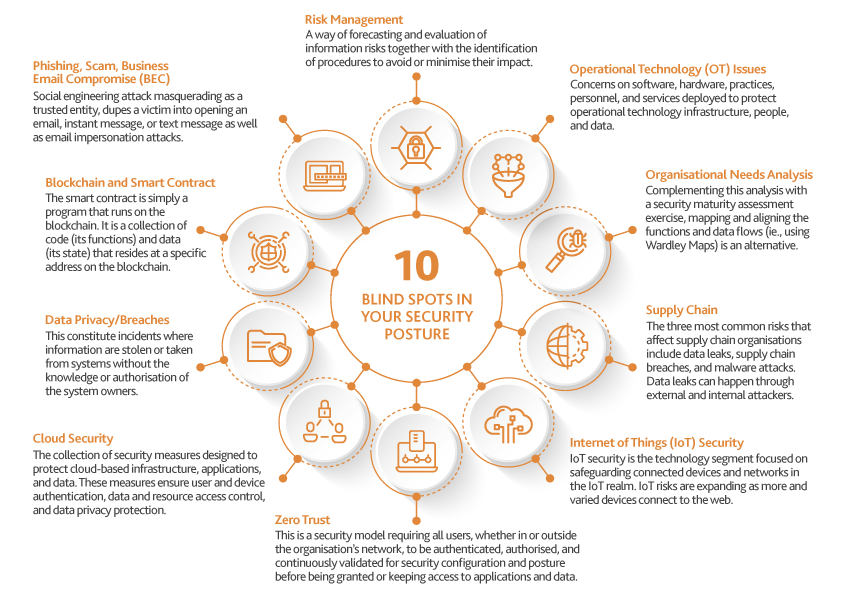
Blind Spots for Cybersecurity 2022
1. Phishing, Scam, Business Email Compromise (BEC)
Are users able/trained to identify customised phishing/scam/BEC emails and messages? Cyber criminals have been relentless in coming up with new ways to carry out cyberattacks such as phishing, scam, and BEC. One such method is to lure the victim to reach out to the attacker by sending emails that do not contain any attachments or malicious links to their victims.
Another method is to send customised links to a specific user. Those who attempt to access the links will not be able to access it without the specific cookies. A variety of technical measures were used (such as contextual advertising and buying of domains that look like the original ones) and display of specific contents to targeted devices via traffic cloaking. Improvements in AI technologies have also made it easier for cyber criminals to tailor messages for the purpose of phishing attacks, scams and BEC alike. As it gets increasingly difficult to detect AI-authored fake content/news, organisations may have to depend on issuing warnings to their employees and try to perform content moderation on their platforms as it is not easy to detect deepfakes from authentic content.
2. Risk Management
Organisations should revisit the contracts they have with their 3rd and nth parties (if available). Are there legacy contracts that have insufficient risk-based clauses that will affect their security posture? Are findings and concerns being consolidated and reviewed at each stage of the vendor’s lifecycle?
With more companies pivoting to cloud, storing of sensitive/confidential information such as customer databases on a cloud-based customer relationship management (CRM) platform exposes an organisation to risk of data being accessed remotely. Organisations may need to consider including nth party risks and the impact of any disruptions it may bring.
3. Operational Technology (OT) Issues
Businesses in regions where threats are driven by specific local or national issues may be exposed to cyber espionage campaigns. This undoubtedly may affect the businesses’ cyber threat profile. However, organisations should be reminded that cyber threats may not be geographically bound but operational considerations are.
4. Organisational Needs Analysis
Third party risk management vendors often provide organisational needs report from a pre-generated format which may not necessary be the true reflection of the status of the intended organisation. Hence, it is important to perform mapping and more in-depth analysis to ensure that it meets the organisational needs.
5. Supply Chain
The dependency or blind trust for open source and commercially made software and technologies exposes organisations to risk in the event of downtime/misconfigurations, or if the software is weaponized by threat actors. Investment in visibility will not prevent disruptions from happening, but it can help organisations to anticipate risks in advance and thus mitigating the effects of the disruptions.
6. Internet of Things (IoT) Security
Do users have the ability to adhere to security, configuration, and application updates, and carry out vulnerability management and identity access management?
While IoT devices have done a good job of providing us with the convenience of completing job functions with a tap of a finger through our smartphones, it is unable to protect our privacy and as well as to keep up with security patches/issues by itself. And with more consumer IoT devices sharing the same network with corporate devices, the organisation’s attack surface has expanded with more places for data to slip through. This has allowed hackers to take advantage due to IoT devices being released with serious security vulnerabilities. Even if the backend technology has been set up perfectly, poor digital habits will still lead to the compromise of a website or a network.
7. Zero Trust
Do organisations have the policies/procedures set up to limit trust violations and flag anomalous behaviour? Will organisations have the visibility and be able to investigate and respond to suspicious events for remote and on-premises environments?
Attacks like SolarWinds have driven home the importance of visibility and the ability to investigate attempts of intrusion/access of data in real time. Visibility is the critical component to define trusted connections and stop nefarious movements in the network. In addition, segmenting the environment can reduce the attack surface and restrict the movements of the threat actor in the network. Improving the resiliency of network does not detect threats coming from the perimeter, and it may take months for Security Information and Event Management (SIEM) and behavioural analysis tools to identify a problem. As such, access control should be enforced through principle of least privilege.
8. Cloud Security
Too many super admins could have been created as organisations adopt Software as a service (SaaS) application such as Dropbox, Salesforce, Slack and G Suite to share information inside and outside of the organisation. This is a security risk as the addition of each admin is akin to an additional endpoint exposed, leading to an increase in the organisation’s attack surface.
The use of SaaS applications also poses a risk when employees who left the organisation retain access to the organisation’s data. Former employees that were not off-boarded properly may pose a risk to the organisation, leading to the possibility of data loss/breach, compliance failures, etc.
9. Data Privacy/Breaches
It has been commonly assumed that data breaches are caused by cyber crimes happening outside the organisations. Hence, organisations often invest on MSSPs, applications and security software or tools and tend to forget to address the social issues, policies or practices and employee trainings related to usage, collection, and detention of confidential and proprietary data.
Organisations should regularly assess the risk profiles of users, endpoints, application, intellectual properties (IPs), etc., and carry out risks assessments to help organisations stay on top of privacy risks to mitigate against reputational and financial loss when a data breach incident occurs.
10. Blockchain and Smart Contract
Organisations should note that data that is to be protected under privacy laws such as General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Health Insurance Portability and Accessibility Act (HIPAA), etc., should not be stored on a public blockchain even if they have been encrypted. The rise of quantum computing leads to an increase in exposure of quantum computer attacks in the future. While it will not break the blockchain technology, data that has been encrypted can be decrypted in far less time than what the traditional computing method offers.
Even without the risk posed by quantum computing, cryptographic risks (e.g., weak/obsolete encryption algorithms) and improper implementation of Software Development Life Cycle (SDLC) still exists and needs to be addressed to prevent blockchain or smart contracts from being compromised, thus improving data protection and business continuity of the organisation.
Code reuse and insecure default software configurations are common vulnerabilities affecting the security of smart contracts. Hence, organisations need to perform due diligence before using a smart contract. Organisations also need to log and monitor their systems to look out for events signalling abnormalities or an attack. However, organisations will become potentially vulnerable if there is no one to monitor the logs.