Strengthening the Cybersecurity Posture with Adversary Emulation
Adversary Emulation
Adversary emulation is a type of red team engagement that leverages on tactics, techniques, procedures (TTPs) that were used by adversaries to mimic real world intrusion campaigns. Adversary emulators build a scenario to test certain aspects of an adversary’s TTPs. An adversary emulation should be based on the adversary TTPs so as to ensure that the adversary attack is more accurate. Cyber threat intelligence, which is the data collected, processed, and analysed to understand a threat actor’s motives and attack behaviors, will be blended in to define what actions and behaviors the red team uses in adversary emulation.
A goal-based adversary emulation will leverage the agreed-upon methods needed to accomplish the identified goal over an extended period. During an adversary emulation, the team will act as adversaries to infiltrate organisation’s network, evade detection by endpoint security devices such as firewall, intrusion detection and prevention systems (IDPS) while pursuing the identified goal. If the red team is detected and stopped, they will think of alternative methods and come out with a new plan of action until they are successful, or an agreed-upon engagement period has been reached.
MITRE ATT&CK Framework
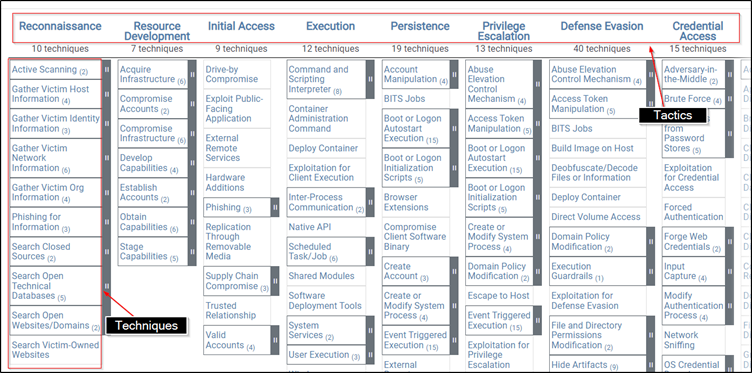
Figure 1: MITRE Matrices
MITRE ATT&CK stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge. It is a very important framework while constructing an adversary emulation plan as it is a curated knowledge base and model for real-world adversary behavior that reflects the different phases of an adversary’s attack lifecycle. Figure 1 indicates the MITRE matrices1 which consist of a set of techniques used by real-world adversaries to accomplish a specific goal. Those goals are categorised as tactics in MITRE matrices. Since tactics and techniques in MITRE ATT&CK have been observed in real-world intrusions, it makes them ideal candidates for adversary emulations.
Cyber Kill Chain
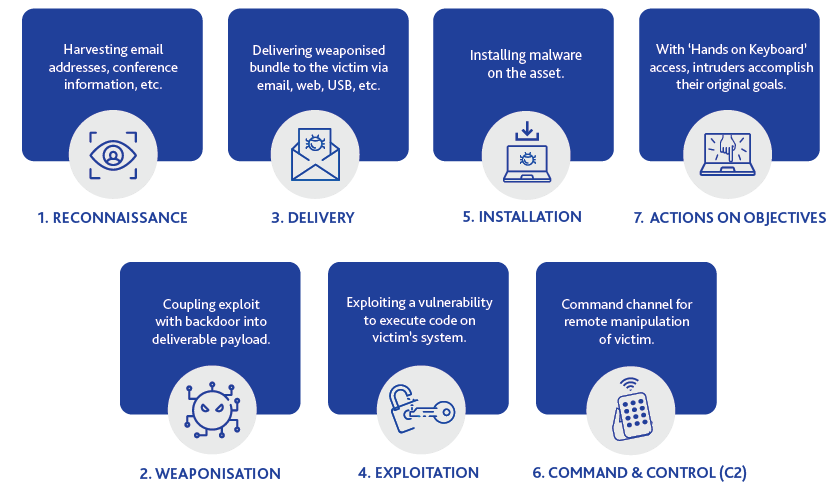
Figure 2: Cyber Kill Chain
Cyber kill chain framework2, developed by Lockheed Martin, is a cybersecurity model that traces the stages of an adversary attack from the early reconnaissance stages to the exfiltration of data. It consists of 7 distinct phases which is shown in Figure 2. This framework makes it easier to understand adversary attacks, security breaches and advanced persistent threats (APTs) and therefore, it can also be considered while crafting an adversary emulation plan.
Adversary Emulation Plans
Adversary emulation plans (AEPs) are the way to prototype adversary behaviors according to a particular set of tactics, techniques, and procedures (TTPs) defined in MITRE ATT&CK framework. For instance, MITRE has created an adversary emulation plan3 for the persistent threat group APT3 and showcases the step-by-step guide to emulate this group along with the TTPs and tools that they have used to eventually compromise a system and exfiltrate sensitive information.
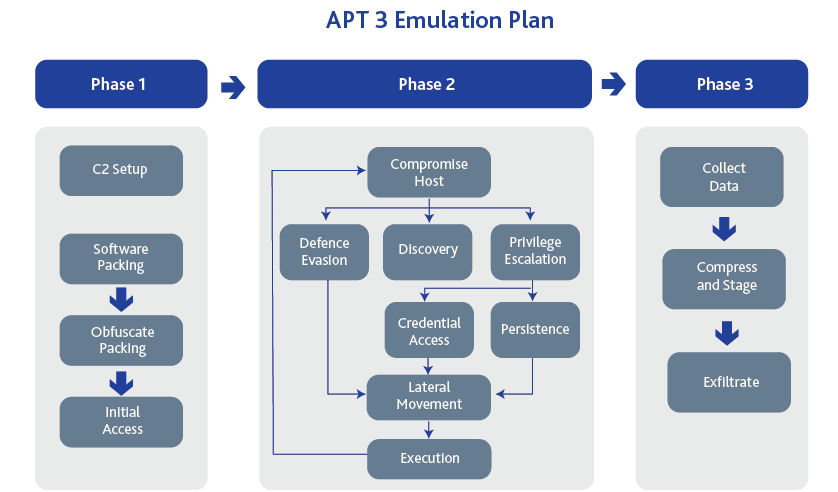
Figure 3: APT3's Three Phases of Action
The APT3 emulation plan is divided into 3 different emulation phases which includes the initial access in phase 1, all the way until the final phase of exfiltrating sensitive information in phase 3. The primary goal for phase 1 is to achieve successful code execution and gain initial foothold of a system within the target environment. Some techniques used in this phase include spear phishing attacks, malicious links or attachments, 0-days vulnerability, etc. The objective for phase 2 is to identify and migrate to desired systems within the target environment with the intent to discover more information like credentials, documents for exfiltration. The actual exfiltration process happens in phase 3.
With AEPs, red teamers can construct an adversary emulation based on TTPs used by certain persistent threat group and launch it against their enterprise security infrastructure in order to fine tune their gaps in the defense before an actual adversary attack happens.
Create an Adversary Emulation Plan
An adversary emulation plan can be created according to the 5-step process4 shown in Figure 4. The detail of each process is documented as follows:
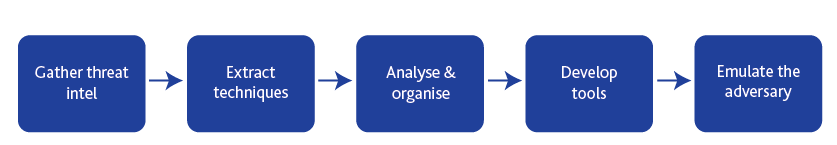
Figure 4: Process for creating an adversary emulation plan
Gather Threat Intel
Choose an adversary which could be a threat to your business and combine what your organisation knows together with publicly available intel to model the behaviors of the adversary and what they go after.
Extract Techniques
Based on the intel that you have collected from process 1, extract the techniques used by the adversary and map them based on the MITRE ATT&CK framework.
Analyse and Organise
Analyse all the techniques used by the adversary and organise them into an operational flow in such a way that it is easy to create specific plans for. For instance, the APT3 adversary plan shown in Figure 3.
Develop Tools
After knowing what techniques your adversary used, it is time to think about how the adversary uses a specific technique, the tools they used for different techniques as well as the procedures they followed so that adversary emulators could replicate those TTPs.
Emulate the Adversary
It is time to perform adversary emulation after all the plan has been set. Adversary emulators should work closely with the blue teamers to find gaps in the defense and figure out why those gaps occur in the first place. After that, adversary emulators should collaborate with cyber threat intelligence team to determine the next threat and repeat the process over again.
Benefits of Adversary Emulation
The key advantage of adversary emulation is to identify security gaps, assess and evaluate how resilient an organisation is to withstand against specific adversary techniques and attacks. Organisation can also use adversary emulation to find out which part of their network is more vulnerable for an attack based on TTPs used by real-world adversaries and prioritize those threats which are most relevant to them.
Another advantage of adversary emulation is that it breaks down the barriers between red teamers and blue teamers. It makes them collaborate by sharing knowledges on the way to detect or evade a specific adversary attack rather than seeing each other as rivals. This makes both the red and blue team disciplines better.
Adversary Emulation Tools
There are different commercial or open-source adversary emulation tools that offers different functionalities to assess how resilient an organisation is against specific adversary techniques and attacks. Here are some of the adversary emulation tools that are used by adversary emulators:
Atomic Red Team
Atomic Red Team is an open-source tool maintained by Red Canary. It contains a collection of lightweight tests to emulate a wide variety of known adversary techniques and attacks based on MITRE ATT&CK framework. It serves different purposes such as testing the detection coverage, validating visibility and adversary emulation.
CALDERA
CALDERA, also known as Cyber Adversary Language and Decision Engine for Red Team Automation. It is an open-source automated adversary emulation tool that is developed by MITRE. Cyber security practitioners can use CALDERA to build a specific threat profile and launch it in a network to see which part of the network is susceptible of the attack. It also helps to assess the defensive capability of a blue team and train them on how to detect specific threats.
Cobalt Strike
Cobalt Strike is a commercial tool that is created by Raphael Mudge in 2012 to enable threat-representative security assessments. It is a threat emulation tool with powerful post-exploitation agents and covert channels in order to emulate threat actors quietly embedded in target’s network. Adversaries increasingly use this tool to conduct cyberattacks because of its user-friendliness and obfuscation capabilities. It also has the ability to conduct spear phishing attacks and gain unauthorised access to target system. Besides that, this software is highly customisable and can be removed without leaving any evidence behind, thus making it the preferred tool for adversary emulation.
How to protect your business from adversaries
Besides conducting adversary emulations to assess the resiliency of your business to withstand against adversary attacks, here are some other tips to protect your business from adversaries:
- Patch your systems regularly. It is important to upgrade your systems diligently as some patches fix critical security bugs that could potentially be exploited by adversaries to gain unauthorised access to your systems.
- Implement 2-factor authentication. This authentication scheme requires users to provide additional information besides their login credentials such as a one-time password (OTP) that is sent via SMS. 2-factor authentication can also be served as a second defense mechanism if your credentials were leaked accidentally.
- Limit the information you put online. Adversaries often use techniques like Open-Source Intelligence (OSINT) to gather public information about their targets and use the information gathered to launch social engineering attacks such as phishing attacks.
- Enforce the least privilege principle. All accounts should be given minimum access level that is needed to complete the task. This can minimise the potential damage from any cyberattacks.
- Change the default credentials for network devices and smart devices. Devices like routers should not be left with default credentials as these devices could be a potential entry path that adversaries take to get into your network.
- Conduct awareness training programs. These programs are designed to help end users and employees realise the role they play in helping to combat information security breaches. For instance, it teaches end users how to spot phishing emails to prevent them from clicking on those malicious links to avoid falling trap to any cyberattacks.
- Conduct red team exercises regularly to gauge the security posture of your organisation. Red team exercises simulate the real-world attacks by replicating the TTPs used by real-world adversaries. These exercises can be used to test the preparedness of your security team to defend against real world cyberattacks and to identity any security gaps.
Summary
Adversary emulation mimics the tactics, techniques and procedures used by various persistent threat groups so as to assess the ability of an organisation to withstand against adversary attacks. At the same time, it also fine tune the gaps in the defense before an actual adversary attack takes place. MITRE ATT&CK framework and cyber kill chain can be used while constructing an adversary emulation plan. Furthermore, the 5-step process can be used while creating an adversary emulation plan to model adversary behaviors according to a particular set of TTPs defined in MITRE ATT&CK framework. Besides that, adversary emulation should be conducted in a continuous fashion as the TTPs used by threat actors evolve from time to time.
References
1https://attack.mitre.org/matrices/enterprise/
2https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
3https://attack.mitre.org/resources/adversary-emulation-plans/
4https://medium.com/mitre-attack/getting-started-with-attack-red-29f074ccf7e3#:~:text=For%20those%20unfamiliar%20with%20it,behaviors%20the%20red%20team%20uses.