Protecting from Phishing Scams in Singapore
Cyber crimes have become an increasing cause of concern even before the pandemic period. It has not been a good start to 2022 for at least 469 people who have fallen prey to phishing scams involving Bank A*, with reported losses totalling at least $8.5 million3.
While technology has eased fund transactions, it is also a double-edge sword in facilitating cyber criminals in carrying out fraudulent transactions. In the case of phishing scam involving the mentioned Bank A, the modus of operation has been largely identical to many phishing scams. Victims received unsolicited SMSs purporting to be from the bank, claiming that there were issues with their banking accounts, and they had to click on a link to resolve the issues. The link led the victims to the trap where they were asked to key in their Internet banking account login credentials to resolve the issues. The victims only realised about the scam when they received notifications that there were unauthorised transactions in their bank accounts which by then, have already resulted in monetary losses.
Phishing scams and signs of phishing
Phishing is a method where cyber criminals attempt to acquire sensitive personal information. They often disguise themselves as a legitimate individual or reputable organisation through email, instant messaging, and other communication channels. Once cyber criminals have obtained the required sensitive information, their end purpose is to steal money from their victims. Some signs to look out for in potential phishing scams include:
1. Mismatched and misleading information
Cyber criminals will attempt to mislead you into believing that the information you see is genuine. The key to spot a phishing attempt is to study the information closely. For emails, look out for the sender’s email address that may appear identical to an official email address. Hover your mouse cursor over links in emails to observe a small window which will appear above the link to show you the actual URL. Mismatching links is a strong indicator of an attempt to phish. If you are using a mobile device, long-press the link to display a window with the actual URL1. Do not open any link that you are unsure of.
For websites, cyber criminals can easily create phishing websites that look visually identical to legitimate websites. To distinguish the two, take note of the URL in the address bar of your web browser. Cyber criminals often use tricks such as substituting letters in a URL to mislead you into thinking that you are on a legitimate website.
2. Requests for confidential information
One of the most common phishing methods is when a scammer has created a fake landing page that recipients are directed to by a link through email or mobile to request for sensitive information. The fake webpage will have a login box or request that a payment has to be made to resolve an outstanding issue.
3. Suspicious attachments
If an email with an attached file originated from an unfamiliar source, the attachment should be opened with caution. If the attached file has an extension commonly associated with malware downloads (.zip, .exe, .scr, etc.) – or has an unfamiliar extension – the file should be virus-scanned before opening.
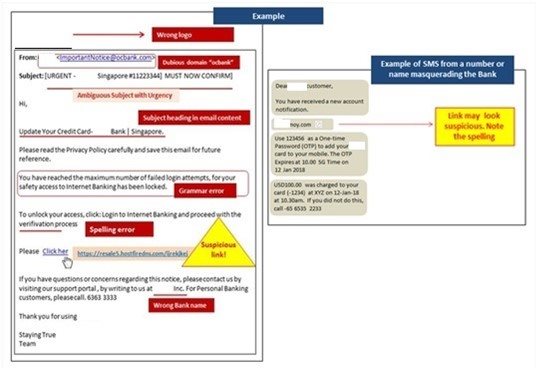
Figure 1: Signs of Phishing scams
How to protect yourself from phishing scams?
1. Staying updated on phishing techniques
Cyber criminals are becoming more innovative with their phishing techniques with the advancement of technology. There is always a chance to fall prey to a phishing scam without knowledge of these new phishing techniques. Keep a lookout for news about new phishing scams as it lowers the risk of getting entrapped by one4. For IT administrators, organising frequent security awareness training and simulated phishing for all users is highly recommended in keeping security a priority throughout the organization4.
2. Be vigilant before clicking anything
Clicking on any links that appear in random emails and instant messages is not a smart move as it puts you at potential risks. Hover over links that you are unsure of before clicking on them2. Ask yourself if it leads you to where it supposed to. A phishing email may claim to be from a legitimate company, and it may look identical to the real website when you clicked on it. The email may ask you to fill in some information, but the email may not include your name. Most phishing emails will start with “Dear Customer” so you should be alert when you come across such emails. When in doubt, check the source thoroughly.
3. Install an anti-phishing toolbar on web browser
Most popular Internet browsers such as Chrome are easily customizable with anti-phishing toolbars. Such toolbars run quick scans on the sites that you are visiting and compare them to lists of known phishing sites. The toolbar can notify the user upon detection of any malicious site. This is an additional layer of protection against phishing scams which allows the user to have ease of mind.
4. Verify a website’s security
It pays to be vigilant when supplying sensitive financial information online. Before submitting any information, ensure that the website’s URL begins with “https” and there should be a closed lock icon near the address bar. Check for the website’s security certificate as well. Be alert for prompts stating any website that may contain malicious files. Do not open or download suspicious files or attachments from emails or websites. One should be mindful of search engines that show links leading users to a phishing webpage by offering attractive benefits. If the user makes purchases through such websites, the credit card details will be accessed by cyber criminals.
5. Check your online accounts regularly
Any online account not in use for a period can be compromised by cyber criminals. Checking on your online accounts on a regular basis prevent your accounts from being compromised. It is good to also cultivate a habit of changing passwords regularly. To prevent bank phishing and credit card phishing scams, one should check monthly statements for your financial accounts and transaction entries carefully to ensure that there are no fraudulent transactions made without your knowledge.
6. Keeping your browser up to date
Security patches are released for popular browsers frequently to counter any security loopholes that phishers and other hackers inevitably discover and exploit. It is always advisable to have the latest updates for optimal protection.
7. Use firewalls
High-quality firewalls act as buffers between you, your computer, and outside intruders. One should consider two different layers: a desktop firewall and a network firewall. The combination usage of software and hardware firewall can drastically reduce the odds of hackers and phishers infiltrating your computer or your network.
8. Be wary of pop-ups
Pop-up windows often masquerade as legitimate components of a website and often, they are phishing attempts. Many popular browsers allow you to manage pop-ups where you can allow/ block them on a case-by-case basis. If one pop-up manages to slip through the cracks, do not click on the “cancel” button as such buttons often lead to phishing sites. Instead, click the small “x” located at the upper corner of the window4.
9. Never give out personal information
As a general rule of thumb, it is never advisable to share personal or financially sensitive information over the Internet. When in doubt, contact the relevant parties. Most phishing emails will direct you to pages where entries for financial or personal information are required. One should never make confidential entries through the links provided in the emails. Never send an email with sensitive information to anyone and make it a habit to check the address of the website. A secure website will always start with “https”.
10. Use an antivirus software
There are plenty of reasons to use antivirus software. Special signatures that are included with antivirus software will guard against known technology workarounds and loopholes4. It is advisable to keep your software up to date. New definitions are added all the time because new scams are being dreamed up all the time. Anti-spyware and firewall settings should be used to prevent phishing attacks and users should update the programs regularly. Firewall protection prevents access to malicious files by blocking the attacks. By having an antivirus software in place, it will scan every file which comes through the Internet to your computer. This helps to prevent damage to your system.
What to do if you fall victim to a phishing scam?
In the worst-case scenario of falling victim to a phishing scam, make sure to make a police report and call the anti-scam helpline at 1800-722-6688. You may not always be able to get your money back, but you might be able to reduce the damage and take steps to prevent falling victim to a scam again. If you clicked a link that directed you to a site that appeared to look like your bank, email service, or social media account, log in to the real site and change your passwords/ reset your security credentials immediately. One should be mindful not to use the same password for multiple accounts as this can compromise your other accounts as well.
Lastly, report the phishing scam to the service provider as soon as possible. Let the service provider know that you have changed your password and to seek advice to safeguard your information and account. If you have given out your financial information previously, you may need to cancel your existing card and get a new card.
Conclusion
To best protect yourself from being targeted, you need to be careful and use resources to avoid being a victim of scams. It is also important to resist clicking and responding to suspicious material in any way. While banks have the obligation to protect the interest of their customers, it is also important that customers play an active role in preventing cyber criminals from succeeding. Prevention is the best form of defence against scam, and one should always be vigilant against suspicious actions.
*Name of Bank to be masked in accordance with anonymity under PDPA.
References:
1https://www.csa.gov.sg/gosafeonline/Go-Safe-For-Me/HomeInternetUsers/Spot-Signs-Of-Phishing
2https://www.kaspersky.com/resource-center/preemptive-safety/phishing-prevention-tips
3https://www.straitstimes.com/singapore/courts-crime/ocbc-bank-customer-lost-120k-in-fake-text-message-scam-another-had-250k-stolen
4https://www.phishing.org/10-ways-to-avoid-phishing-scams