Understanding the Rising Cyber Warfare Trends in the World
Cyber warfare is usually defined as a cyberattack or series of attacks that targets a country. It has the potential to wreak havoc on government, civilian infrastructure and disrupt critical systems which result in damage to the state and even loss of lives. Cyber warfare typically involves a nation-state perpetrating cyberattacks on one another, but in some cases, the attacks are carried out by extreme organisations or non-state actors seeking to further the goal of a hostile nation.
In a time of growing conflict, cyber warfare is a clear and present threat in conflict between countries. As observed in the recent conflict of Russia and Ukraine in 2022, cyberattacks carried out targeted the power grids, financial markets, and government computer systems, all with potential consequences that are as devastating as any bullets or bombs5.
Motivation of Cyber Warfare
There are numerous reasons nations undertake offensive cyber operations. Offensive cyber operations offer a large variety of cheap and risk-free options to weaken other countries and strengthen their own positions. Considered from a long-term, geostrategic perspective, cyber offensive operations can cripple whole economies, change political views, agitate conflicts within or among states, reduce their military efficiency and equalise the capacities of high-tech nations to that of low-tech nations, and leverage on the access to their critical infrastructures to blackmail them4.
Military
The emergence of the cyber world as a substantial threat to national and global security. Cyber war, warfare and/or attacks have also became a domain of interest and purpose for the Military. Examples of cyber warfare driven by political motivations can be found worldwide. Country R* has been implicated in a number of these incidents, including the attack during the opening ceremony of the 2018 Winter Olympics in Pyeongchang and the much-discussed interference during the 2016 US presidential election3.
Hacktivism
Hacktivism involves the use of computers and computer networks to promote an agenda, and can potentially extend to attacks, theft, and virtual sabotage. Hacktivists leverage on knowledge and software tools to gain unauthorised access to computer systems to draw attention to their cause through well-publicised disruptions of selected targets4. Hacktivist groups such as the Anonymous are often portrayed in the media as cyber-terrorists, wreaking havoc by hacking websites, posting sensitive information about their victims, and threatening further attacks if their demands are not met though their actions have frequently divided opinion with their mode of operations.
Financial Gains
Cyberattacks, including ransomware, can be used to generate income. States can use these techniques to generate significant sources of income which can evade sanctions and perhaps simultaneously harming adversaries. This tactic was observed in August 2019 when it was revealed that Country NK* had generated $2 billion to fund its weapons program, avoiding the blanket of sanctions levied by the United States, United Nations, and the European Union4.
Types of Cyber Warfare Attacks
Cyber warfare attacks are increasingly common these days. A cyberattack is when an individual or an organisation deliberately and maliciously attempts to breach the information system of another individual or organisation with various motives in mind. The list is as followed:
Espionage
It is generally an act of monitoring other countries with the intention to steal secrets. In cyber warfare, it involved sophisticated methods of botnets or spear phishing attacks to compromise sensitive computer systems before exfiltrating sensitive information. It is generally assumed to be carried by major superpowers and an example will be country U* as revealed by Edward Snowden.
Sabotage
Compromising of military systems such as command and control (C4ISTAR) systems that are responsible for orders and communications could lead to their interception or malicious replacement. Hostile governments or terrorists may steal information, destroy it, or leverage insider threats such as dissatisfied or careless employees, or government employees with affiliation to the attacking country.
Denial-of-service (DOS) Attacks
DoS attacks prevent legitimate users from accessing a website by flooding it with fake requests and forcing the website to handle these requests. Perpetrators of DoS attacks typically target sites or services hosted on high-profile web servers such as banks, credit card payment gateways, and even root nameservers. DoS attacks can be used to disrupt critical operations and systems and block access to sensitive websites by civilians, military and security personnel, or research bodies.
Electrical Power Grid
Attacking the power grid allows attackers to disable critical systems, disrupt infrastructure, and potentially result in bodily harm. Attacks on the power grid can also disrupt communications and render services such as text messages and communications unusable.
Propaganda Attacks
Cyber propaganda is an effort to control information in whatever form it takes and influence public opinion. It is a psychological attempt to manipulate the minds and thoughts of people living in or fighting for a target country. Propaganda can be used to expose embarrassing truths, spread lies to make people sway their opinions in a particular direction, or side with their enemies.
Economic Disruption
Most modern economic systems leverage on sophistication of technology. Like cybercrimes, attackers target computer networks of economic establishments such as stock markets, payment systems, and banks to steal money or block people from accessing the funds they need.
Surprise Attacks
These are the cyber equivalent of attacks like Pearl Harbour and 9/11. The point is to carry out a massive cyberattack when the target is least expected, enabling the attacker to breach their defences.
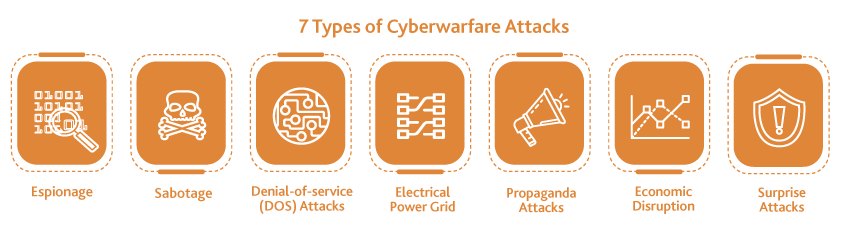 Figure 1: Type of Cyber Warfare Attacks adapted from Impreva2
Figure 1: Type of Cyber Warfare Attacks adapted from Impreva2
Combating Cyber Warfare Attacks
The legal status of this new field is still unclear as there is no international law governing the use of cyber weapons. However, this does not mean that cyber warfare is not addressed by the law.
The Cooperative Cyber Defense Center of Excellence (CCDCoE) has published the Tallinn Manual, a textbook that addresses rare but serious cyber threats. This manual explains when cyber attackers violate international law and how countries may respond to such violations with some guides on combating cyber warfare2.
Conducting Risk Assessments with Cyber Wargames
The best way to assess readiness for cyber warfare is to conduct a real-life simulation of cyber wargame. This allows the testing of governments and private organisations to respond to simulated warfare scenarios which can expose gaps in defence, and concurrently improve cooperation between entities in the following measures:
- Testing different situations – To be well-prepared in detecting attacks in early stages or mitigating risks after critical infrastructure has already been compromised.
- Testing unusual scenarios – Attacks are never scripted and tend to be unconventional. One way is to establish a red team that acts as the attackers and tries to find creative ways to breach a target system. By doing this, it allows the defenders to learn how to mitigate real threats.
- Enhance labour and cooperation mechanisms – Cyber warfare requires many individuals from different organisations and government units to collaborate. A cyber wargame can bring people who do not know one another together and help them decide how to work together in the event of a crisis.
- Improving policies – Establishment cyber warfare policies need to be tested in practice. A cyber wargame can test the effectiveness of policies and provide an opportunity for improving them.
Importance of Multi Layered Cyber Defense Solutions
Under the pressure of cyber warfare, governments of many countries have adopted operational national security solutions to protect their information infrastructure. These solutions typically use a layered defence approach, which includes:
- Application security – Used to test software application vulnerabilities during development and testing and protect applications running in production from threats like network attacks, exploits of software vulnerabilities, and web application attacks.
- Network security – monitors network traffic, identifies potentially malicious traffic, and enables organisations to block, filter or mitigate threats.
- Cloud Security – implements security controls in public, private and hybrid cloud environments, detecting and fixing false security configurations and vulnerabilities.
- Endpoint security – deployed on endpoint devices such as servers and employee workstations which can prevent threats like malware, unauthorised access, and exploitation of operating system and browser vulnerabilities.
- Internet of Things (IoT) security – connected devices are often used to store sensitive data but are usually not protected by design. IoT security solutions help to gain visibility and improve security for IoT devices.
- Threat intelligence – combines multiple feeds containing data about attack signatures and threat actors, providing additional context for security events. Threat intelligence data can help security teams detect attacks, understand them, and design the most appropriate response.
Securing the Private Sector
A secure point in cyber warfare is the resilience of local businesses to cyberattack. Businesses need to tighten their security measures to reduce the benefits of an attack on a nation-state scale. The following is a set of measures to ensure corporate cybersecurity, as well as enhancing national security:
- Prevent breaches to the network through with good cyber hygiene and knowledge.
- Use Web Application Firewalls (WAF) to quickly detect, investigate, and block malicious traffic.
- Prompt responses to a breach and restore business operations as a mitigating measure.
- Facilitate cooperation between the public and private sectors to enhance cybersecurity resilience.
- Reliance on local talents as a resource to help protect against foreign cyber threats through hackathons or bug bounty programs.
Moving Ahead - Recent Efforts Against Cyber Warfare
Governments and the financial industry have a shared interest in countering cyber threats, and this presents an opportunity for collective response and operational collaboration. However, no individual government or financial institution is equipped to counter cyber threats alone1. Some of the initiatives in place for joint effort against cyber warfare includes the Cyber Information and Intelligence Sharing Initiative and Cyber Defence Alliance. It remains to be seen if the effectiveness of such measures as they may be hesitant in sharing of sensitive information among partners.
Summary
For years now, state-funded cyberattacks have zeroed in on learning about weaknesses while stopping short of exploiting them. As technology advances and political unrest continues to fray international relations particularly between powerful countries, enterprises need to do more to protect their systems from falling pretty to cyberattack. Combat in cyberspace is unpredictable and hard to track. As more things are connected to the internet, we will see more such attacks in the real world. But every incident provides lessons for security teams to continue the ongoing fight against cyberattacks.
*Name of Countries to be masked in accordance with anonymity under PDPA.
References
1https://www.forbes.com/sites/forbestechcouncil/2022/02/24/its-2022-is-the-global-cyberwar-finally-inspiring-a-collective-response/?sh=1b9ff4171047
2https://www.imperva.com/learn/application-security/cyber-warfare/
3https://www.itgovernance.co.uk/blog/how-worried-should-we-be-about-politically-motivated-cyber-attacks
4https://lifars.com/2020/03/motivations-behind-cyber-attacks/
5https://www.trendmicro.com/en_us/research/22/c/cyberattacks-are-prominent-in-the-russia-ukraine-conflict.html