Dissecting the Dark Side of the Net
What are your thoughts when you hear the word “Dark Web”? Or if you have heard about it, have you imagined how transactions are being done with the use of computers in this digital age? The Dark Web is known as the core of illegal online activity and its landscape is always evolving. Hence, for organisations that do not keep pace, they will be outdistanced. Drugs, fake documents, personal information, weapons or anything that you could think of are being sold on the Dark Web.
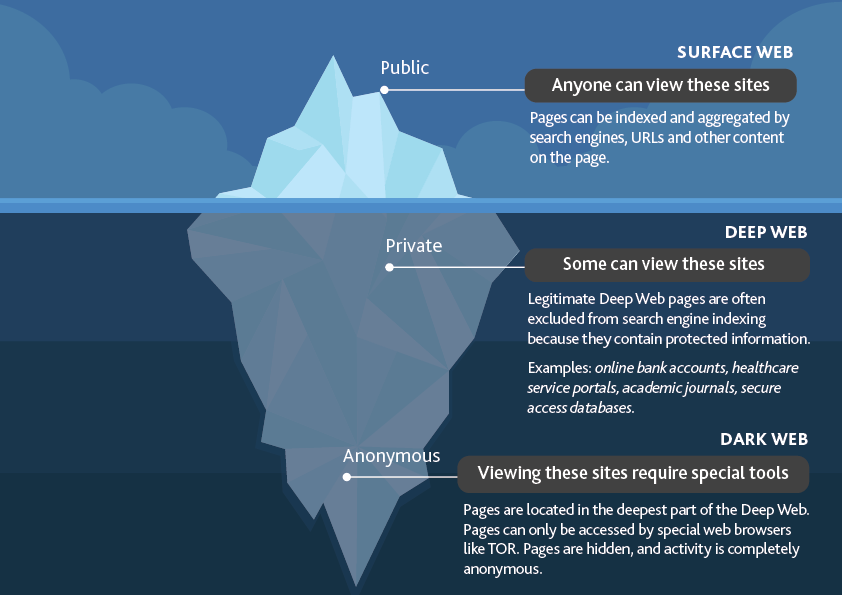
Figure 1 - Surface Web, Deep Web, and Dark Web (image adapted from silverstormsolutions)
How do you access the Dark Web? You will need The Onion Router (Tor). Tor protects the anonymity of its users with multiple layers of encryption. Tor’s reticent sites end in .onion and it is also known as Tor “hidden services”. When this part of the internet is surfed, the use of the Tor browser is required to guarantee anonymity and solid protection of your privacy. Most of such websites are run by fraudsters offering illegal goods from drugs, weapons, or stolen credit cards to forged passports, identity cards, and licenses. Bitcoin is the preferred form of payment on the Dark Web which gives criminals even more certainty to safeguard their identities and whereabouts.
Figure 2 - TOR browser (image created from Jeff's Kali machine)
The Origins of Dark Web
1990s: The Onion Routing Creation
- Onion routing is a technique for anonymous communication over a computer network.
- First developed at the U.S. Naval Research Laboratory by scientists Paul Syverson, David Goldschlag, and Michael Reed.
- It was used to allow freedom of speech and expressions for citizens and journalists who lived under oppressive authorities. It also served to protect whistle-blowers of their anonymity.
Early 2000s - Present: Tor’s Illegal Uses
- While Tor has uses that keep people safe, the anonymity that it provides can be exploited for crime acts. Transactions such as buying and selling illegal drugs, malware, and prohibited content in darknet marketplaces on the Dark Web are often carried out with Bitcoin or other cryptocurrencies which are unregulated and difficult to trace back to the user.
June 2011: The Silk Road Gains Popularity
- The silk road caught the attention of customers, law enforcement, and politicians. Sen. Chuck Schumer, D-New York, called for an investigation by federal authorities including the Drug Enforcement Administration and Department of Justice to shut the site down. Ulbricht claimed he sold the site to someone and he was no longer Dread Pirate Roberts at the time of his arrest and subsequent conviction. Many heard about the Dark Web for the first time through the story of Ross Ulbricht and the Silk Road.
The Silk Road:
- In 2013, 29-year-old Ross Ulbricht was arrested by the FBI for running a website called Silk Road. On the site, people from around the world could buy and sell illicit drugs, weapons, poisons, and services such as computer hacking anonymously and securely without potential traffic monitoring. In 2015, Ulbricht was found guilty and sentenced to two double life sentences plus 40 years without the possibility of parole.
- Ross Ulbricht’s letter to Judge Katherine Forrest prior to his sentencing: “I created Silk Road because I thought the idea for the website itself had value, and that bringing Silk Road into being was the right thing to do. I believed at the time that people should have the right to buy and sell whatever they wanted so long as they weren’t hurting anyone else… Silk Road was supposed to be about giving people the freedom to make their own choices, to pursue their own happiness, however they individually saw fit.”
2013: The End of The Silk Road
- In mid-2013, He was charged with money laundering, computer hacking, and conspiracy to traffic narcotics. It was alleged that he offered a total of $700,000 for hitmen services to take out people who were trying to blackmail him, but he was never charged for these allegations due to the lack of evidence.
Challenges
The following are some of the challenges that users and law enforcement face when it comes to using the Dark Web:
- Lack of awareness, literacy, and skill on the technology.
- The distinct characteristic of the technology where it prevents tracing the one committing the illegal activity and where it is being done.
- The complexity of investigation in a "place" where there are no archiving and no clear-cut jurisdictional lines.
Dark Web is a perfect platform for criminals to camouflage their illegal activities and to remain undetected which makes committing crimes inevitable. A person would likely encounter someone with a fake identity or information which is known as a scam. Once the online transactions are done on Dark Web, the level of anonymity is further strengthened. Ensuring the identity and location of the sender, as well as the destination of information, will be untraceable.
The Dangers of the Dark Web
Dark Web has gained a bad reputation for the prevalence of widespread illegal contents and the media has blown these stories out of proportion. However, there is a grain of truth in the stories, and the following are some points to note:
- It is unattainable to stop or detect all the attacks or breaches as attackers are more flexible and knowledgeable these days. They also have enough funding for hacking and the attempts/ malware infections can be purchased on the Dark Web as there are criminals selling HaaS (Hacking as a Service), offering illegal access to systems for a fee.
- Online scams. Scams on Dark Web markets are as common as are ones performed by independent sellers.
- Having your information uploaded and displayed on unsecured servers like Personally Identifiable Information (PII), such as their social security information and bank account numbers. When such information is published on the Dark Web, it will put the clients and investment firms at risk.
- Beware of click baits or executable links.
- Innocent people accessing illegal sites or using illegal content that they are not aware of, and these actions may lead them to future arrests by law enforcement.
Threat Intelligence on the Dark Web
The Dark Web is identified by its obscurity and disguised nature where cybercriminals regularly sell massive amount of stolen data and that includes login credentials, proprietary code, and intellectual property. In 2020, over 18 billion raw identity records passed through the Dark Web. All a buyer needs are a Tor browser and some Bitcoin, and they can start “shopping” right away. While these are huge cybersecurity concerns for organisations, they can also empower the organisations to extract threat intelligence. By monitoring these dark web sources, organisations can understand the latest threats, place them in the context of their cybersecurity infrastructure and take proactive action to strengthen them.
What is Threat Inteliigence?
Threat intelligence is the knowledge and tooling that enables organisations to understand their cyber threat landscape, and prevent or mitigate attacks to their networks, systems, or applications using data collection.
Threat intelligence is not simply data. Rather, it is contextual data that can help you make informed security decisions by understanding more about:
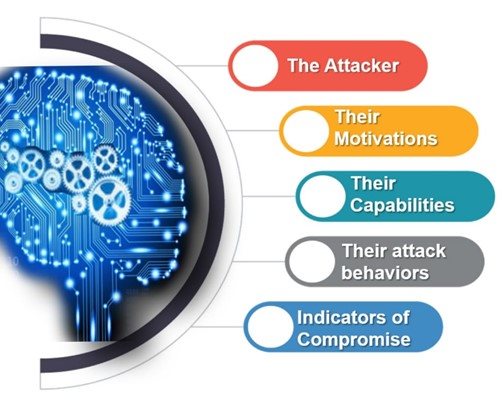
Figure 3 - Contextual data (image created by Jeff and content acquired from flare.systems)
By leveraging on threat intelligence, organisations can proactively fight threat actors and data breaches, and even enable their security teams to advance further than the cybercriminals.
Types of Threat Intelligence on the Dark Web
It is important to know the type of threat intelligence as some of these focus on specific areas and others are broader in their approach. By using specialised dark web threat intelligence tools, things can be easier as they already have access to constricted marketplaces.
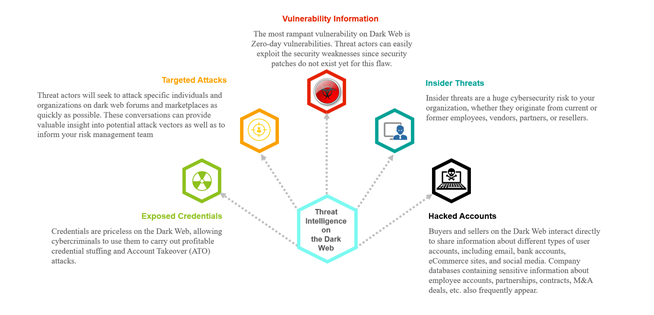
Figure 4 - Types of Threat Intelligence on the Dark Web (image created by Jeff and content acquired from flare.systems)
Benefits
Privacy is essential to many innocent people. Dark Web on its good side, enables the communication of human rights activists and whistle-blowers around the world. Let us also not forget that the governments of some countries are oppressive towards their citizens, and they limit their freedom of expression on the Internet. Dark Web could become freedom’s most important ally.
Importance of Threat Intel on the Dark Web
The importance of Cyber Threat Intelligence for organisations’ strong security posture is widely acknowledged across every sector leveraging on digital transformation. In identifying the threats, organisations will need to optimise intel from the criminal underground. Cyber Threat Intelligence could help in understanding new threats that are going around and keep them on the lookout.
Summary
Since dangers exist on the Dark Web, it is vital to take the necessary precautions. Setting a goal, making plans, and staying focused will help to maximise the benefits from the wealth of information and other services that the Dark Web could offer. Most organisations do not have Threat Intelligence, and this may impose a risk to the organisation when there are targeted attacks. Latest attacks, malware, hacking as a Service, and other illegal services could be purchased through the Dark Web.
We (BDO Cybersecurity Team) over the years has been helping clients across several industries including life sciences, energy, telecommunications, real estate, financial services, healthcare, manufacturing, and public sector by providing cyber security services like incident response, network penetration testing, physical security, application security, and security research. BDO also helps clients to better understand and manage IT risks, identify, and uncover digital trails of misconduct.
References
Dark Web in ten minutes: A quick guide how to stay anonymous using TOR network Kindle Edition by Paweł Winowicz (Author).
Hands-On Dark Web Analysis: Learn what goes on in the Dark Web, and how to work with it Paperback – December 26, 2018 by Sion Retzkin.
https://www.justiceclearinghouse.com/resource/understanding-the-dark-web-challenges-case-studies-for-justice-professionals/
https://www.identityiq.com/digital-security/the-origins-and-history-of-the-dark-web/
https://flare.systems/resource-center/blog/dark-web-threat-intelligence/#:~:text=By%20leveraging%20threat%20intelligence%2C%20you,even%20get%20ahead%20of%20them